
(Advanced Analysis)
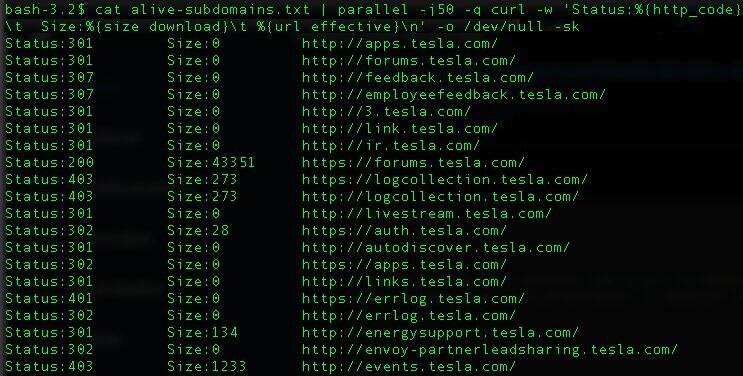
Stage 1: Deep Reconnaissance & Reverse Engineering. The engagement began with targeted reconnaissance of
the application's API endpoints. Static binary analysis of the client-side application revealed
undocumented endpoints handling serialized objects. I utilized advanced fuzzing techniques and manual
source code review to identify a legacy library vulnerable to insecure deserialization, a vector
completely missed by automated scanners.
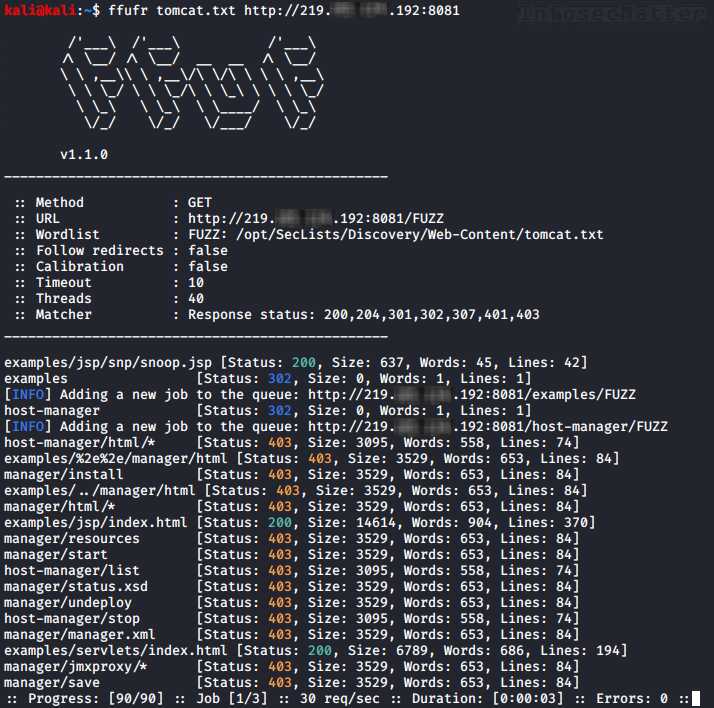
Stage 2: Gadget Chain Construction & Exploitation. Discovering the deserialization flaw was only the
first step. To achieve RCE, I had to bypass strict egress filtering and WAF rules. I constructed a
custom gadget chain that leveraged existing classes within the classpath to execute arbitrary system
commands. This sophisticated payload allowed me to exfiltrate sensitive data via DNS tunneling, proving
the critical impact of the vulnerability without triggering standard defensive alerts.
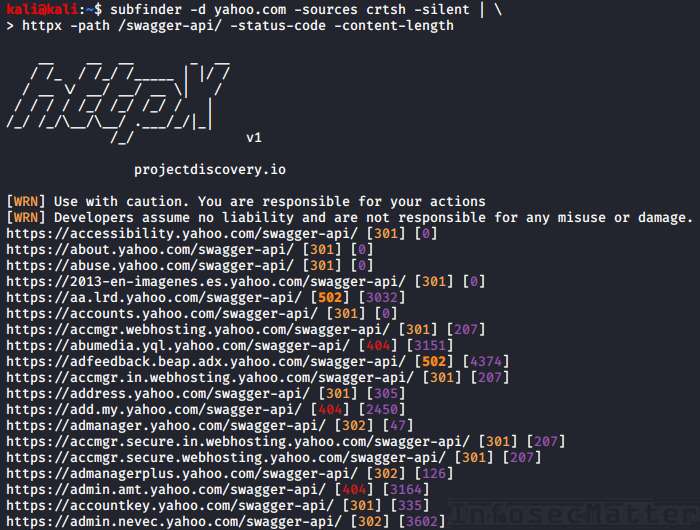
(Bug Bounty Track Record)
Year
Platform
Severity/Reward
Profile Link



(Offensive Toolkit)
Tool / Language
Purpose
Burp Suite Pro
Web Application Proxy & Fuzzing
Python & Go
Exploit Development & Automation
IDA Pro / Ghidra
Binary Reverse Engineering

